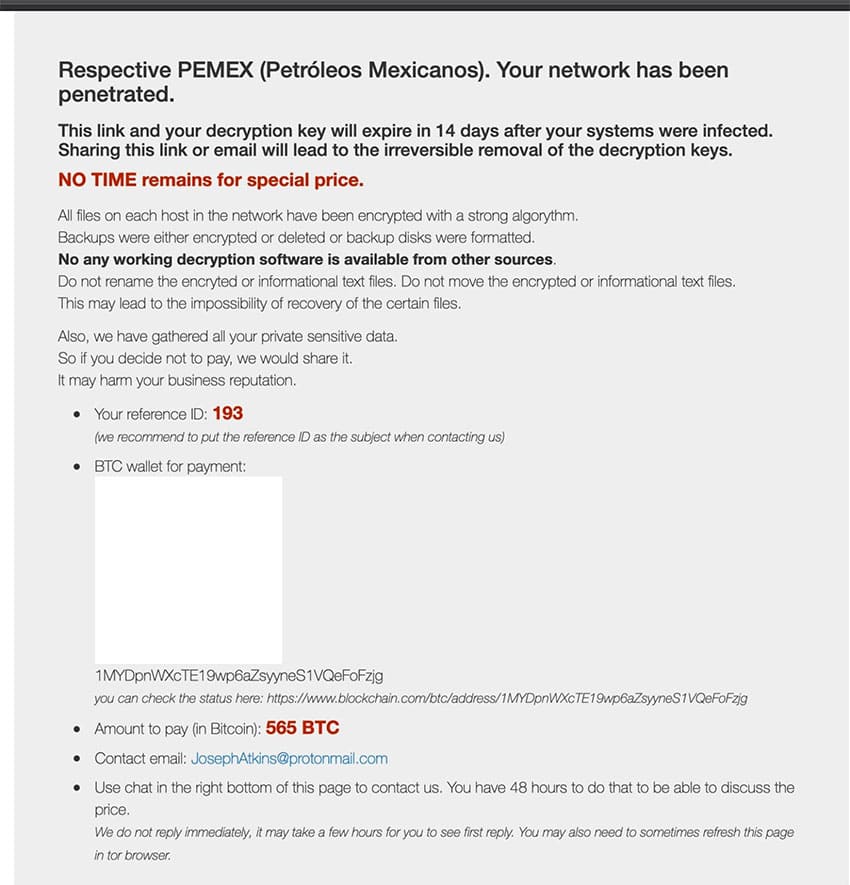
Hackers have demanded a payment of almost US $5 million in bitcoin from Pemex after a cyberattack on the state oil company’s systems on Sunday.
According to the news agency Reuters, a ransom note that appeared on Pemex computers pointed to a dark net website affiliated with DoppelPaymer, a type of ransomware.
It demanded Pemex pay 565 bitcoins, or just over US $4.9 million, within 48 hours in order to have the ransomware removed.
The ransom note said: “Your network has been penetrated. This link and your decryption key will expire in 14 days after your systems were infected . . . We have gathered all your private sensitive data. So if you decide not to pay, we would share it. It may harm your business reputation.”
It also listed an email address to contact.
Reuters wrote to the address and received a response from the suspected hackers stating that Pemex had missed the deadline for a “special price,” apparently referring to a discount.
The state oil company said the cyberattack affected fewer than 5% of its computers and that its storage and distribution facilities were operating normally.
However, several workers told Expansión that Pemex didn’t reveal the true extent of the attack.
The hack, which Pemex said it detected on Sunday, forced the company to shut down computers across Mexico and froze systems such as payments, sources told Reuters.
Employees told Expansión that as many as five in seven computers are affected in some locations. The computer network at Pemex Tower in Mexico City was also breached.
One employee said that Pemex was forced to communicate with workers using the WhatsApp messaging service because they couldn’t open their emails.
“In finances, all the computers are off, there could eventually be problems with payments,” the anonymous source said.
Other sources told the news agency Bloomberg that the cyberattack was disrupting Pemex’s billing systems. They said the oil company is relying on manual billing that could affect payment of staff and suppliers and disrupt supply chain operations.
Invoices for fuel delivered to gas stations on Tuesday from Pemex storage facilities were done manually.
Some employees at Pemex’s refining division couldn’t access the internet on Tuesday and their computers were operating slowly, Bloomberg said.
A source in Villahermosa, Tabasco, said that well-drilling services employees were told on Tuesday that they could start their computers but not log on to the network. Telephone lines weren’t working and workers were unable to access email and Skype.
Employees at the Pemex refinery in Salamanca, Guanajuato, told Expansión that administrative activities had come to a halt since Sunday because they had been unable to use their computer system.
“Here in Salamanca, not even the telephones are being used because they were also connected to the network. They’re transmitting data via radio and working with paper backups,” one employee said.
Cyberattacks on the computer systems of large companies are becoming increasingly common but the ransomware allegedly used in the Pemex hack is relatively new.
However, it is not the first time that it has been used to target a large computer network. According to cybersecurity firm CrowdStrike, DoppelPaymer was behind recent attacks on computer systems at Chile’s Ministry of Agriculture and the town of Edcouch, Texas.
CrowdStrike vice president of intelligence Adam Meyers said that DoppelPaymer attacks are typically made against “high value targets” and executed at a time when they need their systems to be “up and running.”
Therefore, those targeted may feel compelled to pay a large ransom, he said.
A source told Reuters that Pemex was reconnecting unaffected computers to its network on Tuesday and wiping infected computers clean.
The company has not commented on the ransom demand but cybersecurity firm MalwareHunter Team, which has investigated the cyberattack, confirmed that Pemex did not comply with the 48-hour deadline.
President López Obrador said Wednesday morning the attack was not serious and blamed it on interests that were resisting changes brought in by his administration. He said he would not discount the possibility that “conservatives” were behind it.
“. . . they are capable of anything.”
Whether Pemex pays the ransom or not, the hack could take a heavy toll on the state oil company’s finances.
After it was hit by a ransomware attack in March, Norwegian aluminum producer Norsk Hydro refused to pay the hackers but had to spend US $71 million to repair its systems. The company has so far only recovered $3.6 million from insurance.
Computer forensics expert Andrés Velázquez told Expansión that even if Pemex paid the ransom “there is a possibility that the malware won’t be eliminated and weeks later, an attack could occur again.
“Once a system is infected, there is not a lot that can be done but where there is a lot of work to do is in prevention. Unfortunately, what we’ve seen from this government is that cybersecurity. . . is not a priority,” he added.
Velázquez, CEO of the digital investigation firm Mattica, said that the attack should serve as a “wake-up call” not just for Pemex but for all public and private companies, especially those that manage critical infrastructure.
According to the Organization of American States, Mexico is among the least prepared of its members to confront a cyberattack that affects critical infrastructure.
The hack of Pemex’s systems comes seven months after a cyberattack on five Mexican financial institutions during which 300 million pesos was stolen via fraudulent transfers.